Monthly Main Meeting Highlights
August 2017 Main Meeting
Tonight, we had two guests. Armourcard and Malwarebytes.


First up we had a presentation from David.

David is a member who volunteers at the Crows Nest Computer group. He was looking for volunteers to help on a “one to one” basis solving general computer problems, problems like how to find and use an Android app. Any volunteer will get 4 ½ hours free parking. Contact Bob at dbs@cnccc.org.au or 0455 655 451
Then Armourcard’s Tyler Harris

made a welcome return to the stage to show us the latest innovations from Armorcard. Tyler first showed us the product in February 2015
Tyler started with a run-down on data thief. He said “every bit of data is worth something on the dark web”. Those phishing e-mails that can look so legitimate are designed to fool you into giving away your data. That lead Tyler to emphasize these points about data safety.

Don’t click on links unless you are sure their source is legitimate. If you check the URL of the address it should become obvious that the link is not from the real web site of the corporation or bank. The banks, the ATO, none of these would ask for your personal details. Two of the most common scams have been the Federal Police and the ATO. The Police or the ATO will not threaten you. It’s what Tyler called “social engineering” by those defrauders attempting to intimidate us into disclosing our details.
ATM skimming is must more sophisticated now. In times past they may have had a camera filming your pin entry, now its heat sensors. A few tips Tyler suggested, starting with tapping things, has a false cover been added? Jiggle the hole for the card for example, if it moves find another ATM. If the ATM has Tap and Go use it, because the thieves can’t read the card if it doesn’t go through a reader. Place your hands over the keyboard as it destroys the heat signature on the keypad.
This new “tap and go” technology allows you to simply tap your card on a reader. The reader uses, near field communications or NFC on a frequency of 13.5 MHz . Marvellously simple but to quote Tyler “if it (tap and go) was so secure why is it limited to $100?”. For the banks, the profit is in the transactions. Every time you use a card there’s a transaction fee, either for the merchant, for you or both of you. The loss from fraud or theft while important to the bank is a minor problem compared to the profit on transaction fees.

Credit card skimming is a huge business and anyone with an android phone and access to a free scanning app can do it. There are three stages to card reading. The NDF, the chip and the old magnetic strip. If the Tap and Go fails, you resort to the chip and if that fails, you use the magnetic strip. However once you need to use a reader you are vulnerable to being skimmed. Once the card has been skimmed the info can be transferred to the magnetic strip on any old card. Tyler used the example of a magnetic strip on a hotel room key. This is real fraud, once they have created a fake card from their scan they make up a new pin and they are off and running and once they have your card details they can start stealing your identity.
This is where Amourcard comes in.

It’s not the passive technology of metal cases and aluminium foil. They can fail; a simple pin hole in the aluminium can allow the scan to penetrate to the card. Armourcard is an “electronic micro jammer”, it creates a 10 cm force field around it to block any scan. To sell Amourcard in the US they needed Federal Communications approval as jamming is illegal. They had similar problems in China, no government likes to give up its own surveillance needs. Once placed in your wallet or purse Amourcard’s field protects you from scanners. To use a card simply remove it from the wallet or place your hand over the button which turns off the field.
Introducing the new Amourcell and how to protect your mobile phone.

Tyler spoke of the amount of data on a mobile phone and how it is now making them the prime target for hackers. Most new phones come with NFC “the same technology used in Tap and Go”. We have all heard of malicious apps, why does that new game need access to my contacts? While some may be easy to spot others are more subtle. Tyler spoke about malicious apps that start running your NFC in the background and skim any card in its range. Then it sends the information back to a malicious site.
Tyler asked “what was the most valuable item on your phone that a for a hacker would want?”. While everything is worth something the real prize apparently is images, harvested from your phone for illicit purposes. Facebook and the other social media sites are shutting down access to images by pornographers so they are looking to unprotected mobile phones for content. What they do is photoshop young fresh faces onto existing salacious photos, making the subjects look new and younger.
Amourcell is designed to “close the backdoor” of your phone, the NFC connection. While ever your phone is in use NFC is always on. Now the NFC signal is weak, as the name says its “near field” so a hacker can’t easily get a signal whilst walking around the mall. The preferred method now is a high-powered router teamed with a portable sniffer. Once an open NFC is found the router sends a signal to the phone to get it to download a backup of the contents, and Bang, all your data and passwords are cloned and your identity stolen. The new passports also have NFC. As Tyler pointed out 100 points gives them your identity.
The Amourcell unlike the Amourcard has no battery. It comes with a stick-on back and you simply stick it to the back of the phone or the case. It takes power from the NFC chip and only activates if it detects a scan.

The Amourcell unlike the Amourcard has no battery. It comes with a stick-on back and you simply stick it to the back of the phone or the case. It takes power from the NFC chip and only activates if it detects a scan.

To use the NFC feature on the phone simply hold your finger over the button and tap and go.
You can hear Alex’s interview with Tyler here
All members have been offered a great discount on both products, see the newssheet of the 23rd of August.
After the break


Andrew Probert, Senior Sales Engineer for Malwarebytes joined us for a look at what makes Malwarebytes unique. Malwarebytes was formed in 2008 by Marcin Kleczynski, the CEO and Bruce Harrison. When only 12 years old Marcin managed to get his mother’s computer infected. To find help he reached out to the local forums and they managed to help him clean-up his mother’s computer. He volunteered at that forum for years while studying at University. Some of the details are in this article.

The kernel of Malwarebytes was written at this time and with Bruce Harrison he founded the company when he was 18. The company opened in Australia in November and Andrew was asked to join the firm.
Andrew started the night with a video showing a ransomware attack. Nothing much appeared to happen until this sign pops up showing the ransomware had been installed.
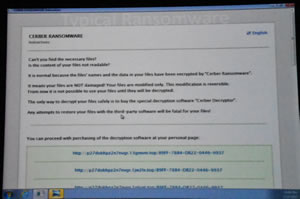
Apparently with ransomware, up to 30% of victims pay up. Andrew gave us some “common sense” ideas about ransomware. Starting with making multiply backups. A reinstall of the backup should see people get their data back. English statistics indicate that a lot of small businesses have no adequate backups and have gone bankrupt once infected.
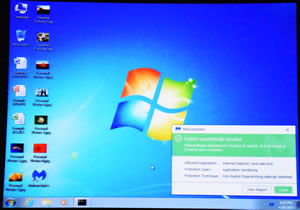
To show Malwarebytes in action Andrew ran us through an infected site and showed just how Malwarebytes protections worked. He started by progressively turning off protection layers.
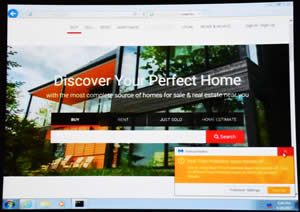
This site had been hacked and was scanning the visiting computer for information. Generally, it was looking for any vulnerabilities it could exploit to hack the visitor’s details. They look for back doors like identifying if your browser can be hacked.
Malwarebytes get around five hundred thousand downloads a day of their free product. Why free? Well it’s about product development. Malwarebytes looks at what protections the client has already and compares them with Malwarebytes. They find that often they are cleaning things the others have missed.
Around “20 % of the time they would find something to clean.” We then had a look at those results. Trojans, rootkits, ransomware and worms were typical of the types of malware picked up. It was not that your preferred anti-virus missed anything but more the case that while they got one trojan Malwarebytes would pick up others.
Another thing Malwarebytes considers is add ware and junk ware. Andrew talked about the school laptops kids bring home full of all those stupid add-ons like menu bars for your favourite browser. Trojans are of particular interest. A banking trojan would compromise your online transactions and if so the bank may well block your account. The big four have been known to ask those who have been compromised to run the free Malwarebytes.
We then had a look at the full Malwarebytes product. Traditional anti-virus protections looks at existing or known infections called pre-execution threats then tries to deal with those that get through the firewall, the post-execution threats.
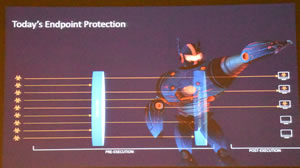
With Malwarebytes there are seven layers of protection and for anything that snuck through Malwarebytes has behaviour modification to check any suspicious activity.
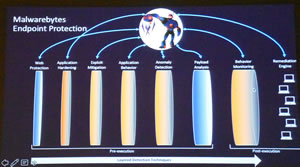
What that does is check on actions that the program is taking. Does it go to the internet? Does it write to files other than its own? Malwarebytes modification behaviour looks for those things and blocks those activities. This is backed up with an anomaly detection layer.

Malwarebytes created this layer by analysing millions of good software programs to find what is considered normal behaviour. They then created a database against which the program can determine if this new program is behaving in a malicious way. If it finds a problem it refers the program back to a Malwarebytes analyser for scrutiny.
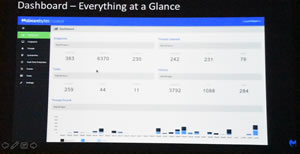
We had a quick look at the dashboard that runs the program
and for those with an Android phone or device Malwarebytes now has a free version for your phone.
Here’s the Malwarebytes Australian site.
and the free version download.
The Raffle
Tonight, thanks to Malwarebytes we had 3 one-year subscriptions to Malwarebytes Premium and thanks to Tyler we had an Amourcard and an Amourcell for our raffles prizes along with a gift card.

Some of our lucky winners.

