Monthly Main Meeting Highlights
Welcome to the November 2015 Main Meeting Our final for 2015
![]()
Tonight Symantec’s Technical Strategist,

Mark Shaw finished the year with a detailed look at how security over the net has changed from the simply anti-virus programs of early years. Symantec’s product range took its name from Peter Norton, the founder of Peter Norton computing. Symantec bought the company in 1990. The product name, “Norton” was retained and Peter became a board member.
The idea behind anti-virus software was to identify malicious code and either block it or remove it. The problem with this idea as Mark pointed out is that the virus makers simply change a part of the code so the anti-virus software fails to recognise it. Anti-virus companies have always played catch up and that made for bloated code in their programs. Symantec was no exception and by 2006 this was a real problem for them. To quote Mark “the program was heavy, it was slow and took forever to load”. That turned people away and Symantec product management decided a new approach was needed. It junked the whole thing, re-writing the program from scratch. “One million man hours” went into that re-write. The design principles were this:- to install the program in less than a minute, to uninstall it in less than a minute; and to make it transparent to the user. The idea behind that was “we are the Security Company”, we should know how to deal with the threat.
It was common for the program to ask the user “What should we do?” but they realised that the ordinary user may not know what to do. So, while the user can still determine what level of control they need, by default the program will simply to inform the user of the actions taken. Mark then looked at the threat landscape, pointing out that Security software is the only IT field with an “active adversary” trying to undermine your work. The main threats Mark spoke about were Ransom Ware, Unwanted applications, Phishing, and zero day vulnerabilities.
Unwanted applications are all those programs which attach themselves to a
program you need. A typically example may be that free file converter which
came with a registry inspector and a new search bar for your browser. As
Mark pointed out while they may not necessarily be malicious you appear to
be paying for very little action and dare I say a new level of annoyance.
Phishing or fishing for information has primarily been the domain of e-mail.
Mark showed recent examples such as an Australian Federal Police speeding
fine, Office of State Revenue tax notices, Unpaid Energy Bills, even an
Australia Post collection notice. Vulnerabilities?

All were false demands for payment, and are attempting to get you to release your account details. They may even be ransomware, which Mark spoke about later. All of them direct you to some fake site which looks very much like the real thing. The new twist in this tail is that phishing attacks have expanded into social media. Now the attacks are appearing as “special offers” on your Facebook page, on twitter and Instagram. Mark considered it an obvious progression as social media makes inroads into e-mail as the main contact media.
Zero day vulnerabilities are where a hacker has identified a way into a program or application that the maker doesn’t know about. Common programs under threat are Java, Flash, browsers and Office programs like Outlook. In the early days the hacker would use this vulnerability to highjack the computer. Now zero day vulnerabilities are on the rise as a black market has arisen in the sale of these discoveries. The finder may not have a use for it but someone who does will pay for the information, sometimes in the hundreds of thousands. These vulnerabilities are exploited in targeted attacks against companies and governments with some Nation States appearing among the culprit’s. They use these vulnerabilities to gain information or to disrupt the work of the organisation they have hacked. Sometimes consumers can be the target but are always the victims until the patch is found.
Ransom ware is malicious software that encrypts all the document files on a computer, denying the user access to their photos, e-mails, and all the other documents. The computer still operates as the system files are left intact. The hacker then demands a ransom to supply the key to unlock the files, which is why the hacker leaves the computer functioning.
The Symantec stats indicate there were 8.8 million attacks in 2014 globally. In the Asia Pacific Japan region Australia is the number one target. How much is the ransom? A typical demand is around three to four hundred dollars. It’s a sweet spot for ordinary consumers. Business on the other hand have a typical payout of twelve to fifteen hundred dollars. Mark discussed how anyone could create a ransomware demand, assuming they can find their way into the black market. This underground market will supply them with lists of potential victims for around three thousand dollars and supply the code for about the same price. The return in a month is around eighty thousand dollars.
Ransomware is not new, Mark showed us the code for one of the first attacks. In 1987 before the internet, one enterprising person distributed floppy disks to participants at a World Health Organisation conference.

The notice asked you to pay for the software but unlike todays trial software which stops working this one froze all your files, He asked a hundred and eighty nine dollars paid by bank draft cheque or international money order payable to PC Cyborg Corporation. When he was caught he said the money went to AIDS research.
Mark continued with a look at some of the current ransomware campaigns. These attacks are very similar to the phishing attacks he showed earlier with campaigns featuring the AFP, the Office of State Revenue and other known brands. The difference this time, is the payload is an encryption file. These are very targeted campaigns and these days with good spelling and very believable presentation.
The hook is the attachment. The letter tells the victim they need to read the attached PDF to find the details. While it will have a PDF icon, the file is in fact an executable file, sometime but not always with a double extension name. Once downloaded it usually runs automatically.
There was some interesting discussion with the group on ways to avoid the problem. One suggestion was “If you are not expecting it don’t open it” another was “Check the letter” the AFP letter allowed you to “unsubscribe” We wondered why would “unsubscribe” from your parking fine? Another was to note the file number or other details and then go through Google to the authority or company real site and check the details there.
Detecting the malicious code is a challenge. Norton doesn’t read your mail and often there is no attachment. If the link is in the text Norton can’t see it. That said, Mark described how Norton will examine things like, where the mail came from and the prevalence with which that e-mail is received. Norton then applies a reputation rating to the suspect file.
Mark went on to discuss the break points in the ransomware process.
1 you receive the spam e-mail. Norton doesn’t look at the mail and mostly
the mail has no content or “payload”, so be suspicious.
2 You need to
click on the link, check where it goes
3 You need to download the
malware
4 Often you need to install the malware. With Norton, it
is hoped that at any point in that chain Norton will kick in and warnings
should show up.
Ransomware is also prevalent on Android IOS and Windows phones. Mark showed us how the scammers even hijacked the camera on a phone to include your photo in the scam.

Symantec have identified 17% of apps available on Android as malicious.

Symantec has collected data worldwide to find this figure. They have looked at over two hundred App stores, not just the Google Play Store, which doesn’t operate in China. Over six and a half million Apps have been analysed. They come in two forms, genuinely malicious software and grey ware. Grey ware are those applications that are not intentionally harmful but eat your battery power, contain excessive and disruptive advertising or collect way too much personal data.
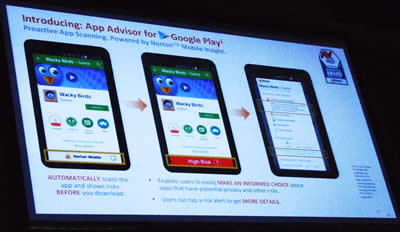
Last year Symantec made the statement “Anti-Virus is dead”. As mentioned earlier the old way to fight malicious software was to find a code and write a block for it. Symantec examine over a million signatures per day and write blocks for them. Ten years ago that would stop over ninety seven percent of the malicious code. Now less than fifty percent are caught by this traditional method.
Just as Symantec had redesigned the Norton software so new methods were needed to combat the ever changing malicious code. So while Symantec still writes code blocks it took at new approach and asked the question “What does this software do?” “Is that action harmful?” Ransome ware for example will disable volume shadow copy which allows you to restore files. This new approach allowed Symantec to identify malicious software other than by its code, which can be changed by its action.
Reputation is another factor in Symantec’s arsenal. The size of the company both in the personal and enterprise environments means it sees over twelve trillion files. As Mark said “we know what’s out there”. That means they can establish a files reputation. They ask questions like, Is this new? How many users are there? Is it signed? What does it do? That means when the user goes to install a new piece of software Norton can pop up and tell them all about the file and gives them the option to continue.
To finish, Mark demonstrated the new Norton Interface.
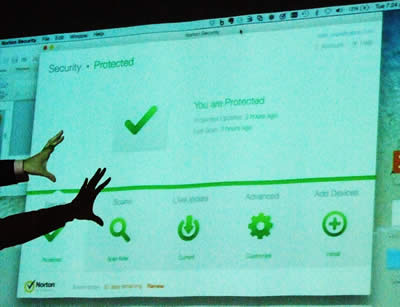
Previously Norton was marketed in around three forms. Anti-virus, Internet Security, and Norton 360. To simplify marketing we now have Norton Security Premium, protection for all your devises, IOS, Android and Windows.

Now Norton offers features like, always up to date software, round the clock security updates and self-service plans so you can change your plan at any time, Web based management and security experts are on call 24/7
The Raffle
Tonight Symantec generously donated

a one device Norton Security Premium to every person who attended, and two

five device licences for the raffle.
Alex found a few fun things to add to the prize pool for our end of year party

And played turbo waiter on the latest hover board device
Our winners

Go to: Previous Main Meeting's Index
