Monthly Main Meeting Highlights
September 2009
![]()
 This
month Alex stepped up to demonstrate Linux Ubuntu Ver 9.04 when iTWire Journalist
David Williams was detained by a more pressing duty, his anniversary.
This
month Alex stepped up to demonstrate Linux Ubuntu Ver 9.04 when iTWire Journalist
David Williams was detained by a more pressing duty, his anniversary.
Linux is 'the other' operating system. Based on Unix it was created by Linus Torvalds and is open source and free. Ubuntu is one of the various flavours of Linux and is the one that has a look and feel most like Windows. Until this version Linux has been a strange mixture of Windows-like performance and DOS type screens. This tended to lessen its appeal to a wider audience. Now, as Alex demonstrated, Ubuntu has removed a lot of the complicated procedures for installation and running applications. It is easy to set up as a dual boot operating system.
Ubuntu comes with a plethora of free applications.
If you need a new application Ubuntu even has a list of what's available in the menus.
Installation is a snack. This version of Ubuntu has eliminated the need to understand Linux code in order to load a program. You simply choose the application, download it and click install.
Then it's ready to run.

 After
the break Trust Defender made a welcome return with the bad news about cyber
crime. Ted Egan and Andreas Baumhof were on the stage to show the group
just how the criminals are attacking even the best-protected sites and exploiting
any minor vulnerability on any computer. Long gone are the days of a hacker
being a pimply face fifteen year-old.
After
the break Trust Defender made a welcome return with the bad news about cyber
crime. Ted Egan and Andreas Baumhof were on the stage to show the group
just how the criminals are attacking even the best-protected sites and exploiting
any minor vulnerability on any computer. Long gone are the days of a hacker
being a pimply face fifteen year-old.
The real threat now is not a simple spam virus but the trojan horse with its mebroot or Master Boot Record root key sitting in the boot-up code of your computer. Most viruses have to wait for the computer to boot, a root key sets code in the boot record and activates before either Windows or your antivirus software has started. It then activates the torpig virus. Wikipedia defines Torpig as:
"a type of botnet spread by a variety of trojan horses which can affect computers that use Microsoft Windows. Torpig circumvents anti-virus applications through the use of rootkit technology and data mines the infected system for credentials, accounts and passwords as well as potentially allowing attackers full access to the computer".
http://en.wikipedia.org/wiki/Torpig
Heres how it works.
Your computer accesses an infected web site.
.
Finding you vulnerable, it attacks.

It downloads the trojan horse, your antivirus will be looking for this download to do something almost immediately so the trojan waits 20 minutes or so until your protection looks elsewhere.

It then copies your master boot record (MBR) to an unpartitioned part of your drive, overwrites the original, and waits for you to reboot.

Your MBR now has a new master and it's not you. Once infected, this sophisticated malware will even update itself to gain access to new information as the criminals change targets. What are they interested in? You, your bank account details, credit card numbers and all your personal identity details. They want to steal your money and your identity.
How?
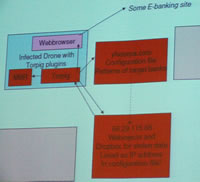
The torpig acts like a plug-in on your browser. The next time you go to your bank's site the torpig adds its own questions to your bank's normal screen.

Sitting in this window are questions your bank did not ask. It looks legitimate. The browser indicates it's from the bank but the data, once you press 'Enter', will go to the criminals, along with your identity. They are also going to use your computer to infect others. All this data is sent back to the criminals' servers, of which you are one once infected.
My friend, a singer song writer has had a web presence for 15 years. About three years ago he received a visit from the Mounties - the Royal Canadian Mounted Police. They took all his machines as his server had been infected and held data of interest to the police. They returned his machines and gave him a new hard drive. So don't think it can't happen to you. The University of California Santa Barbara examined one of these servers for ten days. "Over this period, we observed more than 180 thousand infections and recorded more than 70 GB of data that the bots collected" See the full report at http://www.cs.ucsb.edu/~seclab/projects/torpig/index.html
What does TrustDefender do?
Working with your firewall and antivirus software, Trust Defender examines your computer including your MBR and verifies it's clean by reference to its own server. It watches for the sort of malicious code that directs information away from your financial institution and tells you of you are under attack. To quote their FAQ "TrustDefender acts like a force field. Once activated, TrustDefender creates an encryption 'shield' that temporarily isolates the internet banking session between the member's computer and internet banking server, and enables members to conduct their internet banking with improved safety." Trust Defender is in partnership with some major financial institutions to protect you by defending the banks at their end. You can see how it works with some live demos at
http://www.trustdefender.com/lang-en/products/live-demonstration
The Raffle
Ted and Andreas donated two, one year subscriptions. And Alex supplied three, 32 gig sticks loaded with Ubuntu version 9.04 along with two copies of Norton 360

The winners
Clare and Steve took home Trust Defender


Phillip Soller, Frank Bowman and John Shortland took home Ubuntu



and Mila Vaughan took home Norton 360 along with Maurice Linker who also won the door prize



